10 Super Smart React Tools That’ll Help You Save Time As A Developer

As a React Developer, you can build reusable, standalone bits of code called “React components” and utilize them in your projects. By providing yourself with established web components and suitable react tools to construct your own components, React simplifies and speeds up the process of creating dynamic online applications, which is where its primary use […]
08 ChatGPT Extensions To Supercharge Your Productivity

If you’re here, you probably know all about ChatGPT, the great language model that solves all of life’s greatest questions and is the subject of this piece. But did you know of the wonderful add-ons that enhance ChatGPT’s capabilities? Here are 08 great ChatGPT extensions that supercharge your questioning skills: 1) ChatGPT Chrome Extension Chrome now has an […]
What Should Your Ideal REST API Look Like?

One of the most popular types of modern web services is the REST API. They make it possible for many clients, including browser applications, to interact with a server via the REST API. Because of this, it’s crucial that it be designed correctly to avoid issues in the future. Given that REST APIs are increasingly […]
10 Reasons Why Cloud Computing Is Important For Your Business

Cloud computing refers to the practice of making computing resources, such as data storage and processing power, accessible on-demand without requiring you to perform any administrative tasks. The word often refers to data centers that serve several users simultaneously through the internet. “The cloud” refers to a computing model in which you can access and […]
What Is The ‘final’ Keyword In Java & How Can You Use It?

There are more than fifty reserved words such as keywords and literals that cannot be used as identifiers in java. The ‘final’ keyword in java is a non-access modifier, which is used to control three very specific aspects of classes, methods, and variables. The ‘final’ Classes When a final keyword is added before a class, it makes it a […]
What Is Tailwind CSS & Why Should You Be Using It In Your Coding?
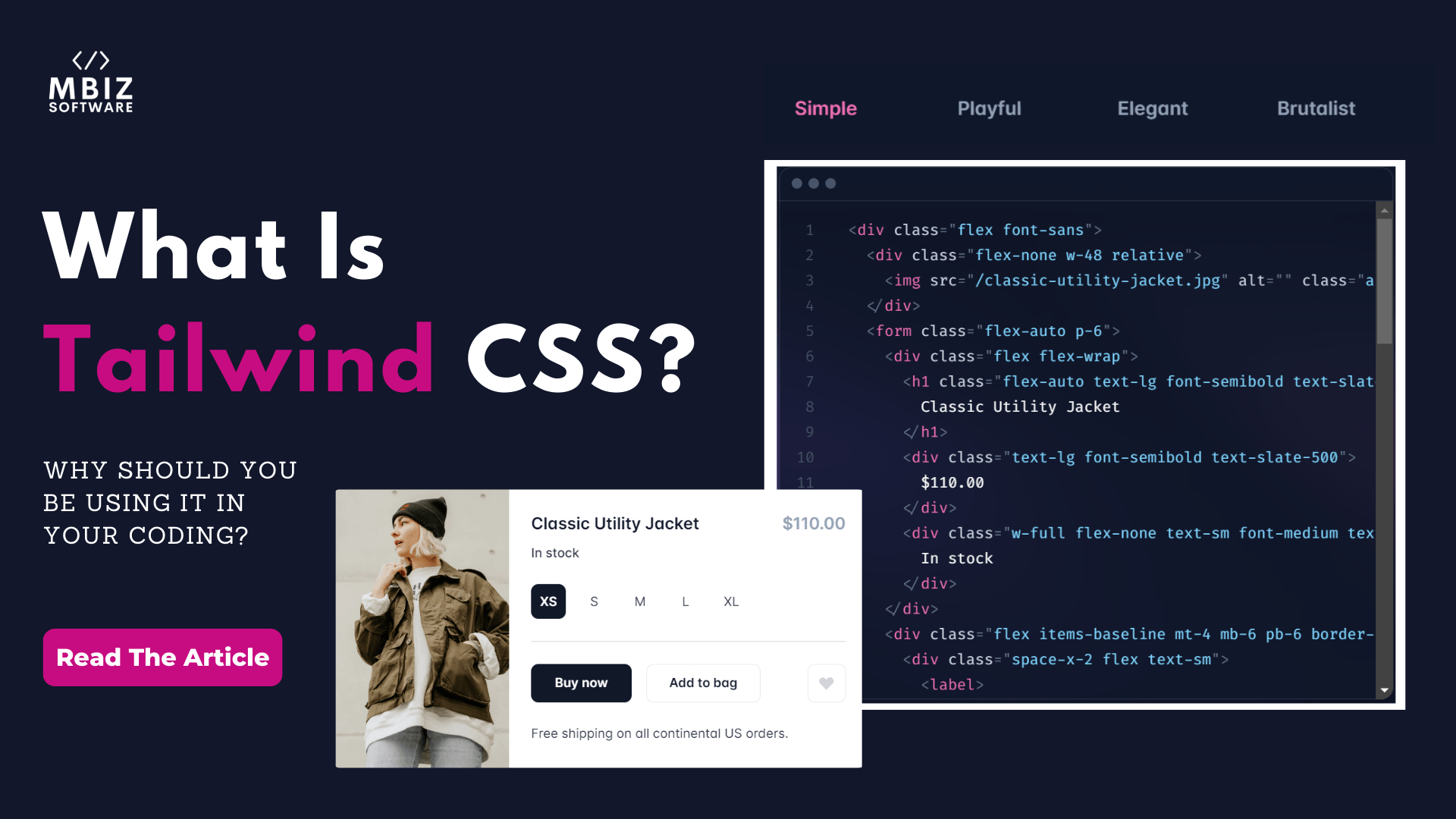
As a software developer, some of the items on your project list would be to build your app or software to be responsive on any device, code that is easy to read and maintain and make your coding easy to work with and not a nightmare to figure it out. Well, with tailwind keeping your […]
05 Benefits Of An IT Managed Services Provider For Your Organization

IT managed services offer businesses an opportunity to focus on their core business functions without worrying about maintaining an IT department or even worrying about their IT needs at all. Outsourcing IT in your organization to a Managed Service Provider (MSP), can reduce your in-house workloads, increase IT efficiency and minimize IT downtimes, through effective […]
MIS vs ERP: What’s The Difference?
Managing a business requires skill and flexibility, to keep functioning with the ups and down’s that one faces daily. What if a business wants to expand and grow its operations; what does it take? With the evolution of technology, businesses can achieve greater reach in all aspects, such as managing core-business processes in real-time, real-time […]
Why The Agile Development Cycle Is The Way For Efficient Software Development

From front-end developers to API innovators, today’s advancements in tools, technologies, and the cloud make it an exciting time to be developing software and services. Over the past two years having gone through the rollercoaster of global events, one of the major shifts we’ve come to realize is how reliant we’d become on digital infrastructure, […]
Is Edge Computing The Way To Go?

Edge computing represents the fourth major paradigm shift in modern computing. The mainframes of the 1950s and ’60s were the first, followed by the shift to the client/server model of the ’70s and ’80s, a model that lasted well into the early 2000s. The cloud was the third major shift, a development pioneered by Amazon’s […]
